Content Security Policy (CSP) is a widely recognized layer of security that aims to detect and mitigate certain types of website attacks. These attacks include Cross-Site Scripting (XSS), data injection, clickjacking, and Man-in-the-Middle (MITM) attacks. This computer security standard was introduced in 2004 and was first implemented in Firefox 4 web browsers. It is also an important part of .NET application development. It ensures that the .NET application is secure.
The standard was originally named Content Restrictions. It is a simple and effective security measure later adopted by all major web browsers. However, it is not supported in Internet Explorer. CSP allows website owners to specify which content sources (such as Images, JavaScript, CSS, etc.) can be loaded on their websites. This is done by adding a standard header to the website's HTTP response.
By doing so, CSP limits which data sources are allowed by a web application. This makes it difficult for attackers to carry out cyberattacks through the browser. Implementing CSP is an effective way to enhance website security and protect your system against various cyberattacks. Its simple implementation and compatibility with major web browsers make it valuable to any website's security measures. Professionals, for instance, the CRM consultants, dealing with the sensitive information of the company, should ensure that CSP is integrated into their system.
+%26+its+Importance.png)
Understanding CSP
CSP is a powerful security measure that enhances your website security by providing an extra layer of protection against various web application vulnerabilities, especially cross-site scripting (XSS). It works by defining the appropriate CSP directive in the HTTP response header, which limits the data sources allowed by a web application. This limits resource loading to only HTTPS protocol, ensuring secure communication between the website and users. CSP also prevents the execution of unsigned inline CSS and JavaScript and dynamic code injection using the “eval()” JavaScript function. The security layer may also be added to the SharePoint collaboration tools for business.
The CSP header can be easily implemented in modern frameworks to enhance web application security. Considering the many applications that use web browsers nowadays, CSP gains even more importance. For instance, organizational Customer Relationship Management Services are accessed using web browsers. Using CSP, website owners can significantly protect against unauthorized access to sensitive data, making their website browser compatible while improving website security. The CSP header defines a whitelist of trusted sources for resources like scripts, stylesheets, and images. Any requests for resources from sources that are not whitelisted are blocked, making it more difficult for attackers to inject harmful code into a website.
Web Application Security with CSP
CSP provides a strong layer of defense against XSS, which is one of the most common web application attacks. It prevents the execution of unsigned inline CSS and JavaScript, which are often used by attackers to inject malicious code into web pages. Only the approved sources are allowed to load resources on a web page. This means that if a third-party source tries to inject malicious code into a web page through an unsigned inline script or style, CSP will block it from executing. In addition to protecting against XSS attacks, CSP also helps prevent code injection attacks by disallowing the use of dynamic code injection techniques, such as “eval().” These attacks should be considered in Mobile Website Development as well.
Dynamic code injection is a common vulnerability in web applications. If the attackers succeed in injecting malicious code into a web page, they can steal data or take control of a user session. CSP can mitigate this vulnerability by restricting the execution of scripts that are not explicitly allowed in the CSP policy. Companies like Google, GitHub, and many more, implement CSP to prevent attacks on their web applications. Google uses CSP to prevent unauthorized code execution on their domains, whereas GitHub uses CSP to protect against code injection attacks on their pages.
Considering that web browsers are now being used in mobile devices, the native mobile application development services are using CSP security in the mobile browsers as well. This includes Android app development services and iOS mobile app development.
Implementing CSP
Below is a step-by-step guide to implementing CSP:
- 1. Define a CSP header in the HTTP response of the web server. The header should include a “default-src” directive that defines the default policy for all resource types. This directive serves as a fallback for other CSP fetch directives.
- 2. Add directives to the CSP header to specify allowed sources for each resource type, including images, scripts, and stylesheets. For example, the “script-src” directive can be used to define which hosts are allowed to execute JavaScript on the website.
- 3. Test the website to ensure all resources are loaded correctly and no errors are generated due to the CSP.
Different CSP Directives
Provided below is a list of some of the different CSP directives:
- default-src - Defines the default policy for all resource types.
- script-src - Defines the policy for JavaScript resources.
- style-src - Defines the policy for CSS resources.
- img-src - Defines the policy for image resources.
- connect-src - Defines the policy for AJAX and WebSockets.
- font-src - Defines the policy for font resources.
- media-src - Defines the policy for video and audio resources.
- object-src - Defines the policy for embedded objects such as Flash.
Common Pitfalls to Avoid When Implementing CSP
If you want to provide .NET consulting Services as Microsoft certified .NET developers, it is imperative that you familiarize yourself with CSP and its integration with .NET software development.
Make sure to test the website thoroughly after implementing CSP. Doing this will ensure that all resources are loaded correctly. Be careful when using the 'unsafe-inline' keyword, as it can undermine the security benefits of CSP. Also, avoid using the 'unsafe-eval,' as it can allow attackers to execute arbitrary code on the website. In addition, be aware of any third-party resources that may be loaded on the website, as they may not be compatible with CSP and could cause issues. Regularly review and update the CSP policy to ensure it remains effective against emerging threats. It is recommended that CSP be used for any application that manages sensitive data. Such applications may include CRM software solutions.
In addition, CSP is also critical for:
- iPhone Application Development
- Android App Development
- Windows App Development
- Blackberry App Development
Examples of CSP Policies
Here are some example CSP policies that can be added to the HTTP headers:
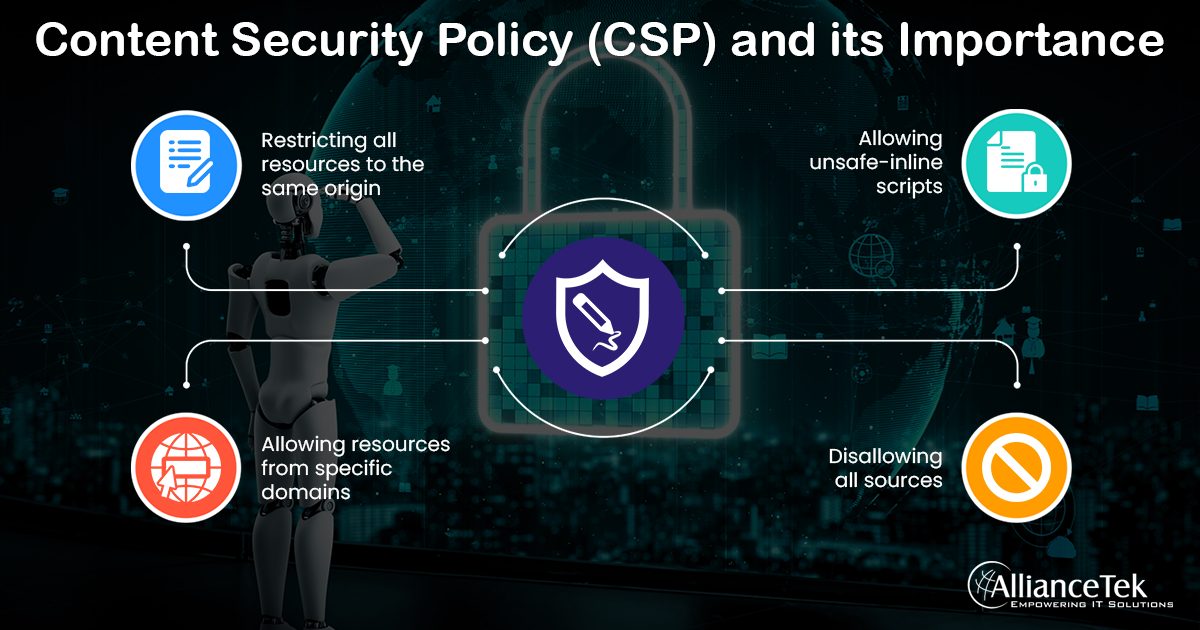
1. Restricting all resources to the same origin
This policy restricts all resources from being loaded from the same origin as the website.
- Content-Security-Policy: default-src 'self';
2. Allowing resources from specific domains
This policy allows resources from specific domains and restricts all others.
- Content-Security-Policy: default-src 'self' https://example.com https://cdn.example.co m;
3. Allowing unsafe-inline scripts
This policy allows inline scripts on the website but restricts all other sources.
- Content-Security-Policy: default-src 'self'; script-src 'unsafe-inline';
4. Disallowing all sources
This policy disallows all sources, blocking all resources from being loaded.
- Content-Security-Policy: default-src 'none';
Final Thoughts
CSP is a web security standard that helps prevent attacks such as XSS by controlling what resources a web page can load. By implementing CSP, web developers can mitigate the risk of malicious code injection and protect sensitive user data. CSP is recommended for web applications that deal with sensitive data like device management consoles, administrative user interfaces, and devices that store user-generated content. When you hire dedicated Android app developers or someone to integrate online collaboration tools, ensure they know CSP and its importance.
Adding CSP to modern frameworks like SharePoint collaboration platform development is very straightforward. However, CSP may not be necessary for static applications without logins or cookies hosted on their own domains or for applications with known issues or previous XSS attacks. It's important to implement CSP based on the specific needs of the web application and remember that it's not a one-size-fits-all solution.



